 Previous
Previous
Smart NICs allow to run user code directly on the NIC and thus “freeing” the CPU from networking tasks.
In this project we will use smart NIC to implement send/receive of TCP protocol for applications running on the CPU.
For that purpose we will modify the VPP networking library to run on ARM based smart NIC and connect them to user application using RDMA.
Project will be implemented in Linux and Bluefield smart NICs hardware.
Prerequisites:
Intro to OS, Networking

GPUFS exposes the host’s file system to the GPU code, enabling self-contained GPU programs to run efficiently, without the need to exit in order to invoke data transfers. GPUFS relies on the CPU for managing its data transfers, a mechanism known as the “host loop”.
The goal of this project is to offload the CPU management overhead to a smart SSD provided by NGD systems, and evaluate its performance benefits.
Milestones:
This work is partially research oriented – milestones may change due to unforeseen circumstances, but the work will strive to achieve the overall best results when pairing a smart SSD with a GPU.

Project description:
MapReduce cluster applications use a shuffle stage to communicate data between mappers and reducers. The project’s goal is to accelerate the shuffle stage communication by offloading packet processing from the CPU to a programmable NIC (Mellanox Innova Flex 4 Lx EN). This includes designing and implementing a reliable transport on an FPGA using high-level-synthesis and integrating it with a MapReduce software implementation.
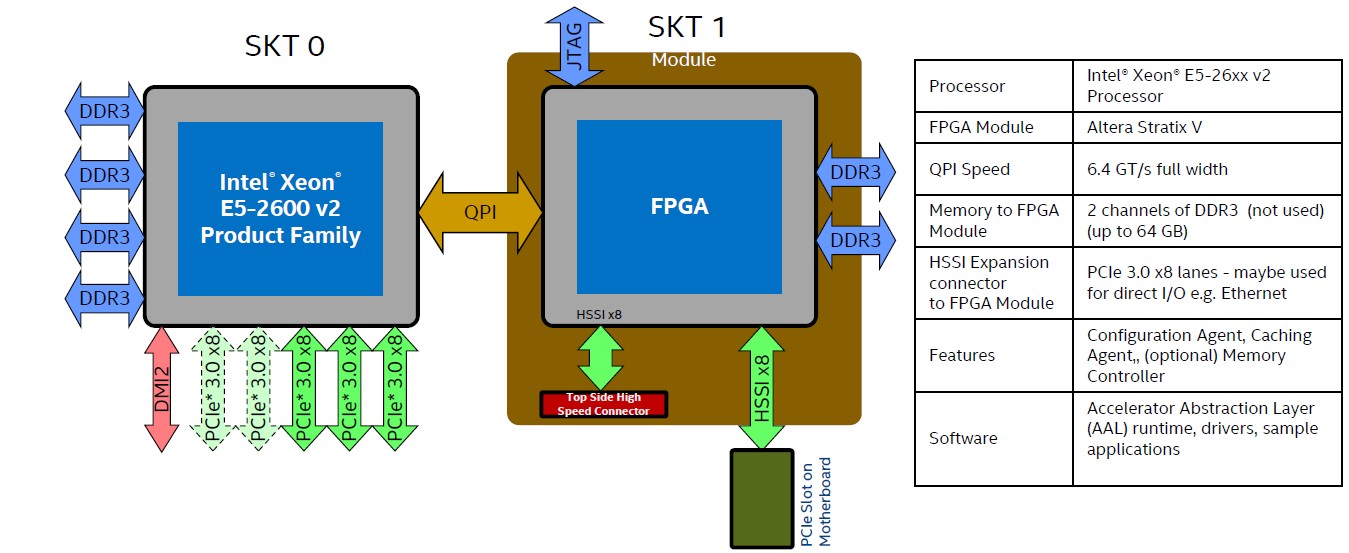
Harp Background
HARP is Intel’s HW/SW development platform for workloads acceleration using Xeon and coherently attached in-socket FPGA (see diagram above).
The FPGA is becoming a first class citizen on the platform, enjoying high BW, low latency, coherency accesses to system memory.
Unlike existing FPGA based accelerators, which usually reside behind the PCI interconnect, the HARP FPGA integration scheme allows the development of new type of BW/latency sensitive accelerators.
The HARP platform is associated with a complete development environment, along with the necessary API, allowing the developer to focus on the accelerator design.
Project Highlights:
1. Meet Intel’s new Accelerator Abstraction Later infrastructure
2. Hands on Altera’s development environment
3. Hands on existing accelerators samples
4. Get acquainted with OpenVX
5. Develop a basic OpenVX accelerator (specific vision function to be determined)
6. Test & validate the design: Compare accelerated vs. non accelerated solutions
7. Project report.
Project infrastructure & requirements:
Intel R2000GZ server (two socket system: xeon & FPGA) running Linux & Altera development tools,
C/C++ experience is vital
Past experience with Verilog is useful
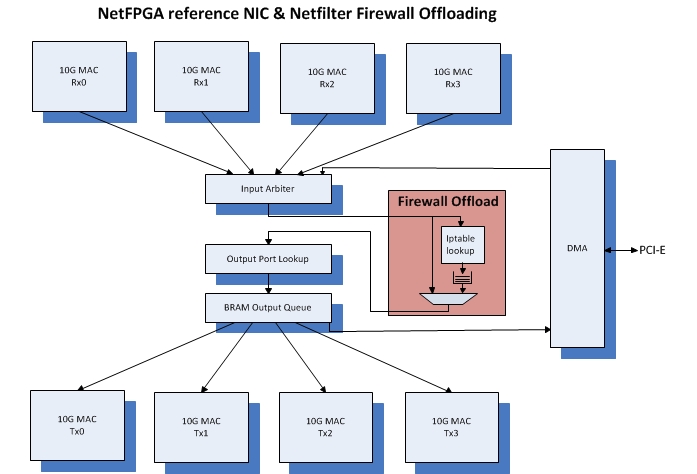
Bump On The Wire: An implementation approach that places a certain network function outside of the system. For example, network related tasks offloading, such as TCP/IP, IPsec, or any other packet related processing.
This project is based on the NetFPGA-SUME platform & reference_nic IP.
The NetFPGA is an FPGA based, open source platform enabling researchers to build high-speed hardware-accelerated networking systems.
In this project, you will implement the Linux Netfilter Firewall (iptables only) within the NetFPGA.
The project highlights:
1. Thorough acquaintance with Linux Netfilter framework.
2. Get acquainted with the NetFPGA board & Xilinx design environment
3. Study the reference_nic IP structure & data_path.
4. Write a project specification.
5. Hands on with off_the _shelf network traffic generator and analyzer (brute, wireshark)
6. Hands_on with the NerFPGA as a NIC.
7. Design the Netfilter Firewall logic and integrate into reference_nic verilog.
8. Test & verify your design: Compare offloaded vs. non offloaded firewall
9. Write a project report.
Project infrastructure & requirements:
Linux-based PC equipped with NetFPGA hardware & Xilinx development tools,
basic understanding of Ethernet switching and network routing
Past experience with Verilog is useful
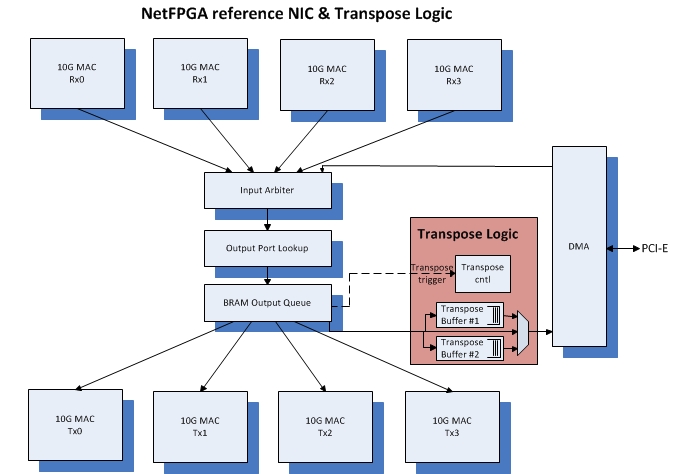
Bump On The Wire: An implementation approach that places a certain network function outside of the system. For example, network related tasks offloading, such as TCP/IP, IPsec, or any other packet related processing.
This project is based on the NetFPGA-SUME platform & reference_nic IP.
The NetFPGA is an FPGA based, open source platform enabling researchers to build high-speed hardware-accelerated networking systems.
In this project, you will implement a Matrix Transpose, which is useful to accelerate some GPU computations, i.e: ArrayOfStructs → StructOfArrays, k-means, word-count.
The project highlights:
1. Write a project specification.
2. Get acquainted with the NetFPGA board & Xilinx design environment
3. Study the reference_nic IP structure & data_path.
4. Hands on with off_the _shelf network traffic generator and analyzer (brute, wireshark)
5. Hands_on with the NerFPGA as a NIC.
6. Design the Transpose logic and integrate into reference_nic verilog.
7. Test & verify your design.
8. Write a project report.
Project infrastructure & requirements:
Linux-based PC equipped with NetFPGA hardware & Xilinx development tools,
basic understanding of Ethernet switching and network routing
Past experience with Verilog is useful
Required courses:COMPUTER NETWORKS AND INTERNET 1 (044334)
Required courses:
Background information:
The student will design a HW based memory scanner, to search for known resident threats (predefined memory patterns), and report its findings.
Memory cleanup is excluded from this work.
The student should be familiar with Linux memory management, paging scheme, virtual/physical addressing, etc.
In addition, a C/C++ programming skills, and possibly RTL programming (verilog) are advantagous.
HARP Background
Intel’s HW/SW development platform for workloads acceleration using Xeon and coherently attached in-socket FPGA.
The HARP platform is associated with a complete development environment, along with the necessary API, allowing the developer to focus on the accelerator design.
Project description:
Design a real-time memory scan for resident malware threats.
The scanner will do a continuous memory scan, with minimum performance intrusion
To be implemented on Intel’s HARP platform, utilizing its cache-coherent FPGA.
The resulting design will then be compared againt a SW-based scanner.
Project Highlights:
1. Meet Intel’s new Accelerator Abstraction Layer infrastructure
2. Hands on Altera’s development environment
3. Hands on existing accelerators samples
4. Get acquainted with system memory scanning
5. Write a SW based memory scan
6. Design a memory scan AFU
7. Test & validate the design: Compare accelerated vs. non accelerated solutions
8. Project report.
Project infrastructure & requirements:
Intel R2000GZ server (two socket system: xeon & FPGA) running Linux & Altera development tools,
C/C++ experience is vital.
Hands on Linux OS memory management & Verilog will be useful

Intel’s Software Guard Extensions (SGX) is a set of extensions to the Intel architecture that aims to provide integrity and confidentiality guarantees to security-sensitive computation performed on a computer where all the privileged software (kernel, hypervisor, etc) is potentially malicious.
References: Intel Software Guard Extensions, Trusted Platform Module
In this project you will work on SGX enclaves found in latest Intel Skylake processors.
You will build an in-enclave secured shared memort infrastructure. This will allow two or more enclaves to share memory with explicit API requests that proves this is a valid sharing.
This will enable new capabilities for enclaves to run preivously unavailable applications that requires the usage of shared memory as part of their code base.
What will do and learn in the project?

Background information:
Ransomware is a type of malware from cryptovirology that blocks the victim’s access to his/her data unless a ransom is paid.
While some simple ransomware may lock the system in a way that is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion, in which it encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
A key observation regarding ransomware activity is that it relies on file modifications to make their data inaccessible to the victim. Therefore, a detection and prevention system may be coupled with the underlying file system to identify potential malicious activity.
References:
https://en.wikipedia.org/wiki/Ransomware
https://thezoo.morirt.com/
https://github.com/libfuse/libfuse
CryptoLock (and Drop It): Stopping Ransomware Attacks on User Data. 2016 IEEE 36th International Conference on Distributed Computing Systems.
Project description:
In this project, the students will implement an online detection and prevention system for ransomware, which will apply different heuristics such as entropy of written blocks, truncation of blocks and threshold-based modifications to certain high-priority directories.
If an attack is detected, the system will notify the user and block the operation, therefore, the potential ransomware activity will not be completed.
The students will use FUSE (File system in Userspace) in Linux that allows fast file system prototyping in userspace with traditional and familiar development tools and IDEs.
The students will evaluate their defense system on real applications and real malware in safe sandboxes to identify the accuracy of the different heuristics as well
as the performance impact on file I/O operations while adding the different detection heuristics.
What will you do and learn in the project?
– Read scientific papers and understand the concept of ransomware and detection heuristics.
– Design, implement and test a prototype for online detection of ransomware.
– Evaluate defense accuracy on benign software and real ransomware.
Required Knowledge
– Operating Systems
– Computer Architecture
– Sufficient programming experience in C/C++.
Status: In Progress

FPGA based smart NICs allow to implement application accelerations running on the NIC and thus “freeing” the CPU from networking tasks. In this project we will use smart NIC to offload JSON parsing for servers using JSON format for communication. JSON is a common format used for flexible and portable transfer of information, but adds additional computational overhead for the server application. We will implement a JSON parsing on the NIC to transfer the data to more efficient for processing format for the receiving application, before transferring the data from the NIC to the CPU.
Project will be implemented in Linux and Innova smart NIC.
Programming languages: C/C++ (using Vivado HLS) and/or Verilog/VHDL
Required courses:

Smart NICs allow to run user code directly on the NIC and thus “freeing” the CPU from networking tasks.
In this project we will use smart NIC to implement send/receive of TCP protocol for applications running on the CPU.
For that purpose we will modify the VPP networking library to run on ARM based smart NIC and connect them to user application using RDMA.
Project will be implemented in Linux and Bluefield smart NICs hardware.
Prerequisites:
Intro to OS, Networking

Project background:
When an application needs to send information over the network, this information is first copied to the OS kernel, and afterwards a second copy is performed from the OS kernel to the NIC.
In order to improve performance we want to avoid this double copy, by writing from the NIC directly to the application memory.
For that purpose we will use a method called TCP header-data split, which is already in use in other contexts.
In our project, the “header” will be written to the kernel space memory, while the “data” will be written to the application memory in user space.
Implementation details:
C programming language.
Linux kernel
Required courses:

Bump On The Wire: An implementation approach that places a certain network function outside of the system. For example, network related tasks offloading, such as TCP/IP, IPsec, or any other packet related processing.
This project is based on the NetFPGA-SUME platform & reference_nic IP.
The NetFPGA is an FPGA based, open source platform enabling researchers to build high-speed hardware-accelerated networking systems.
In this project, you will implement the Linux Netfilter Firewall (iptables only) within the NetFPGA.
The project highlights:
1. Thorough acquaintance with Linux Netfilter framework.
2. Get acquainted with the NetFPGA board & Xilinx design environment
3. Study the reference_nic IP structure & data_path.
4. Write a project specification.
5. Hands on with off_the _shelf network traffic generator and analyzer (brute, wireshark)
6. Hands_on with the NerFPGA as a NIC.
7. Design the Netfilter Firewall logic and integrate into reference_nic verilog.
8. Test & verify your design: Compare offloaded vs. non offloaded firewall
9. Write a project report.
Project infrastructure & requirements:
Linux-based PC equipped with NetFPGA hardware & Xilinx development tools,
basic understanding of Ethernet switching and network routing
Past experience with Verilog is useful

Bump On The Wire: An implementation approach that places a certain network function outside of the system. For example, network related tasks offloading, such as TCP/IP, IPsec, or any other packet related processing.
This project is based on the NetFPGA-SUME platform & reference_nic IP.
The NetFPGA is an FPGA based, open source platform enabling researchers to build high-speed hardware-accelerated networking systems.
In this project, you will implement a Matrix Transpose, which is useful to accelerate some GPU computations, i.e: ArrayOfStructs → StructOfArrays, k-means, word-count.
The project highlights:
1. Write a project specification.
2. Get acquainted with the NetFPGA board & Xilinx design environment
3. Study the reference_nic IP structure & data_path.
4. Hands on with off_the _shelf network traffic generator and analyzer (brute, wireshark)
5. Hands_on with the NerFPGA as a NIC.
6. Design the Transpose logic and integrate into reference_nic verilog.
7. Test & verify your design.
8. Write a project report.
Project infrastructure & requirements:
Linux-based PC equipped with NetFPGA hardware & Xilinx development tools,
basic understanding of Ethernet switching and network routing
Past experience with Verilog is useful
Required courses:COMPUTER NETWORKS AND INTERNET 1 (044334)
Required courses:

Bump On The Wire: An implementation approach that places a certain network function outside of the system. For example, network related tasks offloading, such as TCP/IP, IPsec, or any other packet related processing.
This project is based on the NetFPGA-SUME platform & reference_nic IP.
The NetFPGA is an FPGA based, open source platform enabling researchers to build high-speed hardware-accelerated networking systems.
In this project, you will implement the Linux Netfilter Firewall (iptables only) within the NetFPGA.
The project highlights:
1. Thorough acquaintance with Linux Netfilter framework.
2. Get acquainted with the NetFPGA board & Xilinx design environment
3. Study the reference_nic IP structure & data_path.
4. Write a project specification.
5. Hands on with off_the _shelf network traffic generator and analyzer (brute, wireshark)
6. Hands_on with the NerFPGA as a NIC.
7. Design the Netfilter Firewall logic and integrate into reference_nic verilog.
8. Test & verify your design: Compare offloaded vs. non offloaded firewall
9. Write a project report.
Project infrastructure & requirements:
Linux-based PC equipped with NetFPGA hardware & Xilinx development tools,
basic understanding of Ethernet switching and network routing
Past experience with Verilog is useful

Bump On The Wire: An implementation approach that places a certain network function outside of the system. For example, network related tasks offloading, such as TCP/IP, IPsec, or any other packet related processing.
This project is based on the NetFPGA-SUME platform & reference_nic IP.
The NetFPGA is an FPGA based, open source platform enabling researchers to build high-speed hardware-accelerated networking systems.
In this project, you will implement a Matrix Transpose, which is useful to accelerate some GPU computations, i.e: ArrayOfStructs → StructOfArrays, k-means, word-count.
The project highlights:
1. Write a project specification.
2. Get acquainted with the NetFPGA board & Xilinx design environment
3. Study the reference_nic IP structure & data_path.
4. Hands on with off_the _shelf network traffic generator and analyzer (brute, wireshark)
5. Hands_on with the NerFPGA as a NIC.
6. Design the Transpose logic and integrate into reference_nic verilog.
7. Test & verify your design.
8. Write a project report.
Project infrastructure & requirements:
Linux-based PC equipped with NetFPGA hardware & Xilinx development tools,
basic understanding of Ethernet switching and network routing
Past experience with Verilog is useful
Required courses:COMPUTER NETWORKS AND INTERNET 1 (044334)
Required courses:
